Just got this one finshed, bask in its leetness.


Just got this one finshed, bask in its leetness.

February’s meeting was another one for the books. We had a full blown G+ hangout setup complete with a projector and a hand cam. A big thanks to bneu for providing the cam and darkwind for the capture device. I started the night off by making few big announcements about me and ngharo speaking at THOTCON and how dc414 was picked by OpenDNS as a awesome user group “more on this later”. Then dw5304 informed us of Bucketworks network and finanical situation and I’m proud to say dc414 stepped up right away. bneu is making a huge network equipment donation to Bucketworks, all dc414 donations for the night went to Bucketworks, and dc414 is going to put together a fundraiser for Bucketworks. More on all this later.
I started the presentations off with a big fail on cracking wep “ikr” I felt like a total n00b. I can do it I swear, lol. I did redeem my self by owning a VM system on a PBX by using a 0day I have “No I will not be giving out details on this, other then to those at the meeting and I will never do it again. Its mine!” I didn’t stop there, to further redeem my self I gave a little demo on fimap and opened up a shell on a live compromised server 🙂 The fun wasn’t over yet. Vladimir gave us the 101 on Cat5 cable and a step by step to making your own cables. Then Vladimir and Darkwind had a cable making race and Darkwind smoked Vladimir bad! Thats not all, dw5304 replaced the back light on an old laptop, something I didn’t even know you could do. He took the screen apart and explain each step, then Vladimir schooled us on just how LCD’s and such work. Thank you every one for your hard work!
Thanks to cmoney we have tons of great pictures from our last meeting here. Congrats go out to the free dc414 junk give a way winners, Dan, Darkwind, and to Joel for winning the free THOTCON ticket.
Here is Dan and his new palm one mobile keyboard:

Darkwind and his ALFA 802.11n usb card:

Here is Joel after winning the THOTCON ticket:

Ok thats it, peace out.
I got the Linksys NAS200 a while back to hold all my music, movies, and TV shows. For a while it worked great and I really liked being able to do streaming and shit from it but I soon found out that the HDDs I had inside the unit where getting supper hot, even to the point that you couldn’t hold them. I of course had a to lose a HDD before I figured that out 🙁 I was just a little upset about this so I opened the unit up to find this weak little fan inside that as hard as it tried it just could not keep the drives cool. Then I decided to beef up the cooling system a little by adding another fan to the mix.
So I found 5v PC fan “for the cooling”, a hot iron “to cut/melt a hole for the fan”, a soldering iron and some solder, a screw driver, and hot glue. Now I would like to say I got it all right the first time around, but I can’t. Now the unit it self runs off of 5v so all I had to do was solder it to the board somewhere. My first attempt was a failure. I tried to solder the new fan to the same terminals that the little weak fan was using. While it did power the fan and work, the unit would eventualy stop responding. I figured the fan was drawing to much power to low in the chain. So I opened’er back up and moved the new fan to the start of the chain, I connected it right where the power comes into the unit. The unit it self runs on 5v and the Linksys power supply that came with it only gives out 5v so no worries there. Then all I had to do was put it all back together, hot glue the fan in place to suck the hot air out and turn it on.
My mod works great and it keeps my HDD’s nice and cool now 🙂 The only down side is it makes a little more noise now and I have to unplug the power from the unit to turn the fan off 😛 And now for some pictures.
Here is the hole I made with some info, the stock fan is on the other side of the unit:

Here is the main board:

Another view of the board:

Here is the end result:

Another view of the end game:

K thats it, peace.
January’s meeting had a few kinks but all in all everything went well and we had a few new faces in the crowd. We had some issues with the G+ hangout, but it was our first time and i’m sure it will go smoother the second time around. Then i had video issues while trying to give my LFI attacks demo and had to give a backup demo, but everyone else was awesome.
Darkwind gave his first presentation with dc414 and it was a good one for sure. He showed us some of his modded radio equipment and how to decode all sorts of transmissions, from HAM faxes, pagers, DTMF tones and more being broadcast in the air ways. Talked a little about cell tower emulators and software radios. dw5304 and Klaiviel gave us a run down of how they hacked the new xbox 360 to play ripped games off the HDD in just a few not so easy steps 😛 Then dw5304 have a little demo on resetting passwords on any windows box with just a few key strokes. I gave the last presentation of the night and after my LFI demo fail i was able to give a nice little demo of how the ODiG tool works and how it can aid in pwning networks.
One of the coolest things about the meeting, it was our honor to have Jayson Street join us via G+. We hope to see him at the next meeting. Cmoney couldn’t join us but I was able to snap a few shots here and there which you can view here. The big winner of free dc414 junk was Stephanie, here she is with her winnings: “ALFA usb 802.11n card”

We have added a few achievements here and there and changed how you get badges. We also changed up the badge idea it self a little, now once you finish up the achievements for a badge you get a cloth badge for free and become eligible to buy an electronic badge. Work on the badges them selves are still in the design phase but it is coming along nicely, lots of great ideas flying around. Lastly, thanks to a awesome donation by Black Rat we now have wireless access points for the badge program! Ok that is it for now, get working on pwning your own badge and enjoy.
The badge program project is a little game for hackers, crackers, and phreaks. The goal is to facilitate learning in a fun and interesting way. Each badge has a list of achievements you must obtain to be eligible to get the badge. Some achievements will be as easy as clicking a like button for FB, another might be as hard as having to try and social engineer a password out of a random person. Every time you get a badge you also get a mystery prize!!
The badges them selves are still under development so expect future posts about them as we finish them up. For a list of the badges and their achievements go here. So get started and get your 1337 badge now!
Decembers meeting was awesome! Vlad gave a great in depth wi-spy demo. He showed us what a Bluetooth file transfer looks like, what microwaves look like and access points looks like, and gave good detail of just what exactly was going on. Before the meeting he asked people to bring in any wireless devices to see what they looked like in wi-spy while operating. dw5304 came packing with a some directional wireless access points, one so powerful it completely took over the entire spectrum that wi-spy displays.
Then i gave my presentation on using sql injections to bypass logins to sites and admin areas. I showed what should be sent to the sql server, how it looks in php and how to identify exploits. Then showed what a sql injection looks like when passed to the server. I didn’t stop there, we broke into gmtoday.com to take a look at the news paper, then used a google dork to pwn a few more logins. I also talked about dc414’s new badge program project, more on this later, and announced dc414’s new year eve party! More on this later as well.
dw5304 finished off the presentations with a killer demonstration of just how weak time warners security is. He showed us how to take complete control of one of their cable modems with just a few requests, even how to build your own private proxy network made out of time warner modems! Then to top it off demoed a never ending DoS on a modem, kicking this client off line for as long as he wished!
Other then the normal junk i bring to give away, ngharo donated a portable dvd player for cars and F4r4d4y donated a arduino “thanx guys”. All of which went to a good home. Here are some pics cmoney took at the meeting “thanx cmoney”, and a big congrats to Castor for winning the anti-M$ poster and pantsme on snagging the arduino!
Castor and his winnings:

by dw5304 AT dc414.org
We are creating a network boot environment for installing OS and running diagnostic utilities.
I chose dd-wrt because of its ability to set the DHCP options for the next-server and bootp options easily. For a list of supported dd-wrt routers see here. You can do this from Windows server, Linux, or any other DHCP server that support BootP as well.
If you have issues getting dd-wrt to install please read the information that’s listed on their site for setup. Log into your router, in my case its 10.10.1.1, click on services tab and in the additional dnsmaq options place the following where 10.10.1.5 is going to be your TFTP server.
Additional DNSMasq Options:
dhcp-boot=pxelinux.0,, 10.10.1.5
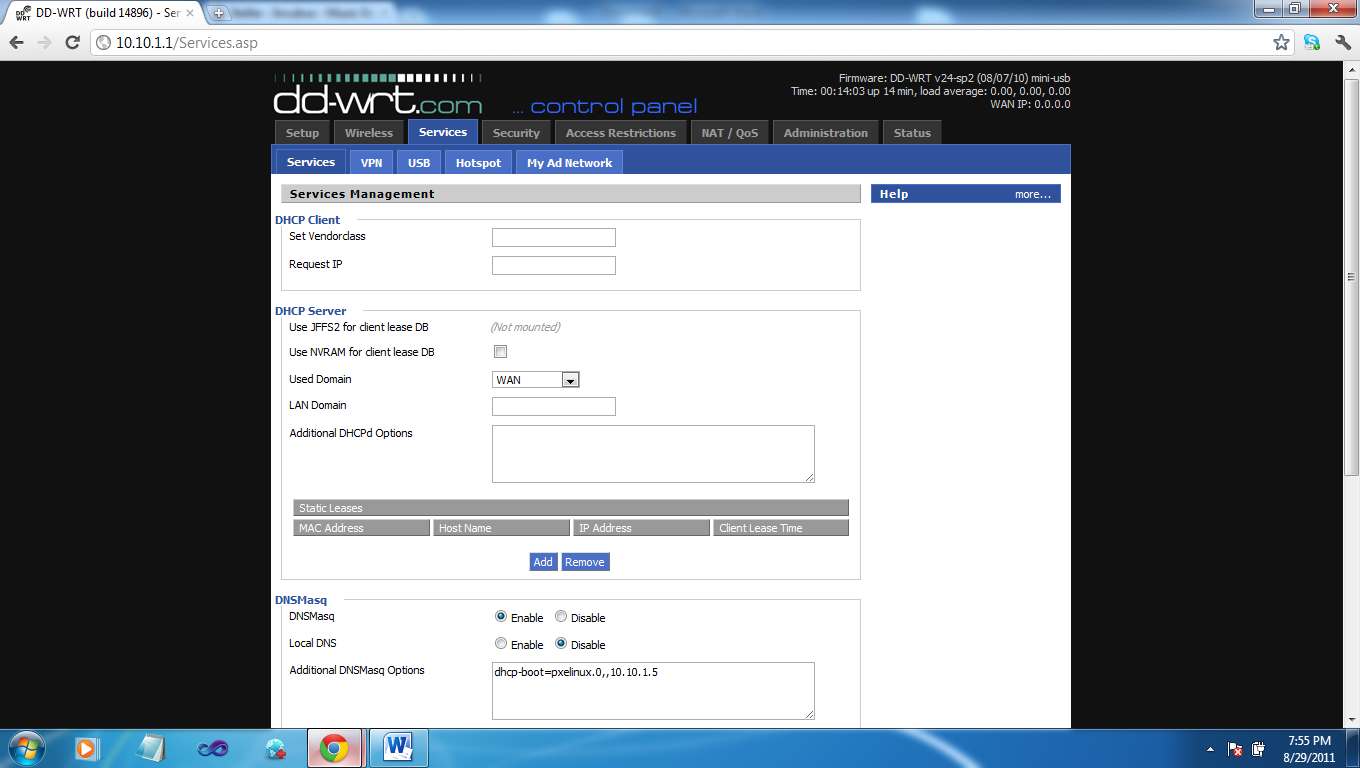
Make sure to hit apply settings and lets continue installing our TFTP server
I am using tftpd for Window: 32bit install, 64bit install.
If we are running Windows we should add tftpd service to the firewall exception list. You can allow a program through the firewall via Control Panel.
Open Ttpd settings and remove all items except for tftp_server and tftp_client, then lets click the tab for tftp set security to none (TFTPd is not an encrypted channel. You should be using firewall ACLs to limit access to the server). Check the box for Option negotiation, Translate Unix file names , and Allow virtual \ . Everything else should be unchecked.
Create a TFTP root directory. In my case I chose C:\tftp-root\. Extract the boot files into this directory. Download files here.
Download the Windows AIK. Burn the image to a disc or mount the ISO and run the Windows AIK setup. You can just hit next though the whole setup process.
Now click on Deployment Tools Command Prompt shortcut on desktop or in your start menu. Now run “copype.cmd Arch C:\DESTINATION” (where ARCH = x86 (32bit), amd64 (64bit), ia64 (Itanium) and DESTINATION is where you’d like the output the data files for the image we will be creating to reside.)
copype.cmd ARCH C:\DESTINATION
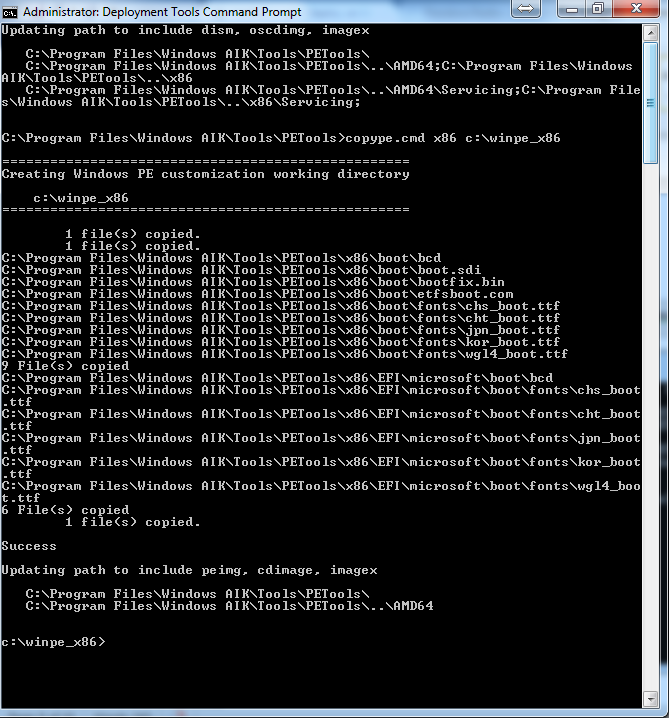 Dumping a x86 image to c:\winpe_x86
Dumping a x86 image to c:\winpe_x86
Mount the image that was created for us. Make sure to replace winpe_x86 with your destination used in the previous step.
imagex /mountrw c:\winpe_x86\winpe.wim 1 c:\winpe_x86\mount
Copy the files for PXE boot to the tftp-root \boot folder.
copy mount\Windows\Boot\PXE\*.* C:\TFTP-Root\Boot
Copy boot.sdi from AIK to the TFTP folder.
copy "c:\Program Files\Windows AIK\Tools\PETools\x86\boot\boot.sdi" C:\TFTP-Root\Boot
Copy pxeboot.n12 to pxeboot.0 so it will work with our syslinux bootloader. Syslinux only seems to take *.0 file extension.
copy c:\TFTP-Root\Boot\pxeboot.n12 c:\TFTP-Root\Boot\pxeboot.0
Next copy bootmgr.exe to the root of the tftp-root folder
copy c:\TFTP-Root\Boot\bootmgr.exe c:\TFTP-Root\
Windows might complain if it can’t find boot.ini in the TFTP root, so let’s create it.
echo > C:\TFTP-Root\boot.ini
We need to create the BCD (Boot Configuration Data) for the PXE environment to load the WIM (Windows Install Media) file’s (this is a great line to use on chicks). Note: I found following Microsoft’s instructions for this step resulted in fail.
bcdedit -createstore C:\winpe_x86\BCD
Bcdedit /store c:\winpe_x86\BCD -create {ramdiskoptions}
Bcdedit /store c:\winpe_x86\BCD -set {ramdiskoptions} ramdisksdidevice boot
Bcdedit /store c:\winpe_x86\BCD -set {ramdiskoptions} ramdisksdipath \boot\boot.sdi
Bcdedit /store c:\winpe_x86\BCD -create /d "Windows 32bit installers" /application osloader
If this is all proper it will return a GUID. We need this in order to create a boot entry.
Now that we have our guid for the windows 32bit installers we need to tell it what to do. If you want to also create a 64bit osloader run the last command again to create a new guid. (Bcdedit /store c:\winpe_x86\BCD -create /d “Windows 64bit installers” /application osloader) with a different description aka “windows 64bit installers”. Replace {guid1} with the guid of your bcd entry mine is {3e04a3b3-dcdf-11e0-894c-d1514d26a539}.Your bcd guid will be different. Make sure to include the {}. If u want to use a different wim file please also update it accordingly.
Bcdedit /store c:\winpe_x86\BCD -set {guid1} systemroot \Windows
Bcdedit /store c:\winpe_x86\BCD -set {guid1} detecthal Yes
Bcdedit /store c:\winpe_x86\BCD -set {guid1} winpe Yes
Bcdedit /store c:\winpe_x86\BCD -set {guid1} osdevice ramdisk=[boot]\Boot\winpex86.wim,{ramdiskoptions}
Bcdedit /store c:\winpe_x86\BCD -set {guid1} device ramdisk=[boot]\Boot\winpex86.wim,{ramdiskoptions}
Now I’m going to add an x64 entry for my boot environment you can skip this setup if u wish.
bcdedit /store c:\winpe_x86\BCD -create /d "Windows 64bit Installers" /application osloader
Bcdedit /store c:\winpe_x86\BCD -set {guid2} systemroot \Windows
Bcdedit /store c:\winpe_x86\BCD -set {guid2} detecthal Yes
Bcdedit /store c:\winpe_x86\BCD -set {guid2} winpe Yes
Bcdedit /store c:\winpe_x86\BCD -set {guid2} osdevice ramdisk=[boot]\Boot\winpex64.wim,{ramdiskoptions}
Bcdedit /store c:\winpe_x86\BCD -set {guid2} device ramdisk=[boot]\Boot\winpex64.wim,{ramdiskoptions}
now we need to create the bootmgr settings. I set my time out to 99999 you can shorten this if u want.
Bcdedit /store c:\winpe_x86\BCD -create {bootmgr} /d "Windows Pe BootManager"
Bcdedit /store c:\winpe_x86\BCD -set {bootmgr} timeout 99999
Bcdedit /store c:\winpe_x86\BCD /displayorder {guid1} {guid2}
Now copy bcd to tftp root\Boot folder by copy C:\winpe_x86\BCD C:\TFTP-Root\Boot
We should now be able to test to make sure everything works in terms of bcd. Start up a new computer, and tell it to boot from the pxe environment. Then hit enter when the syslinux menu show up.
we can see it works! Good job. Now we need to create wim files and the rest of the scripting.
Lets edit the winpe_x86 image we mounted earlier.
We want to edit and make changes to windows\system32\startnet.cmd ( this file is the first thing the WIM file runs. It basically sets up drivers and network access.)
and make it say
wpeinit
main.cmd
W:\scripts\main.cmd
now make a new file in the mount\windows\system32\ called main.cmd
echo >mount\windows\system32\main.cmd
next edit main.cmd and make it say
@echo off
echo mapping drive.
echo trying dc414 pxe setup
net use W: \\ip_or_host\win
echo example of second network try
net use W: \\ip_or_host\win
echo starting main.cmd
W:\scripts\main.cmd
Replace ip_or_host with an ip address or host name. If you have more than one network in your setup you can add another ip or host for the other network. Just do another net use command.
Installing network drivers:
we will go and download the network driver packs from http://driverpacks.net/driverpacks/latest
make sure you download the proper x64 or x86 drivers ( you will need a torrent client to do this). Extract the files to a temp dir in side of the win_x86 folder\drivers now we want to recursively add all the drivers from this driver pack.
Now we add all the drivers recursively into the package.
Dism /Image:C:\winpe_x86\mount /Add-Driver /Driver:c:\winpe_x86\drivers /Recurse
After you get done modifying this image your done with this wim and we need to commit the changes.
imagex /unmount /commit C:\winpe_x86\mount
Now lets copy this wim to our tftp-root\Boot folder
copy winpe.wim C:\TFTP-Root\Boot\winpex86.wim
Lets see if our Wim file we just created boots and works as expected.
It dose we have successfully gotten our wim file to boot. Now we need to setup the share on the windows workstation. Inside the tftp-root folder there is a folder called “win” we need to share this folder with access to everyone. If this is not done you need to specify a user name and a password inside your net use command in the wim image.
Now we need to add our windows installations to this win folder and update the choice menu that boots from the network share…
All that’s needed is the setup.exe and the sources folder that contains the install.wim you can delete boot.wim to save space.
Example of my setup. For win32 entry. Win64 I just change it say 64 instead of 32 and when a new sp comes out I usually add the number to the folder.
When the system boot it runs main32.cmd or main64.cmd (from tftp-root\win\scripts\)depending on what was put in earlier for main.cmd on the wim file. then calls install32.cmd or install64.cmd. These two files contains the menu system for the installer your operating systems. Along with these batch scripts there is also choise64.exe and choise32.exe they run bases on the install script you are running seeing the x86 and the x64 do not include the subsystem that supports each other… you will see a subsystem not support cause of the exe that runs and switches the window… (cmdow.exe) some antiviruses will see this as a virus and will delete it. Its safe, its being detected because of that it dose. It hides the command line window and brings up the setup exe in front of the cmd window that’s open…
To add or edit more entries into the install32.cmd or install64.cmd just add an , and the next number them make an entry for that option.
Now if you want x64 do the same thing but replace all instances of x86 with x64 or 32 with 64.
And then copy the winpe.wim to winpex64.wim to the C:\tftp-root\Boot folder. If we want to boot to an iso for other diagnostic tools we need to add entries to C:\tftp-root\pxelinux.cfg\default its easiest to add a menu to go to another menu to make it easier and cleaner. Place a new file in the c:\tftp-boot\menu folder usaly I make them end w/ a .cfg so u can edit them menu system. For instance lets add a menu system to give us options to run a hdd test.
Open C:\tftp-root\pxelinux.cfg\default
now lets add an entry for this hdd diag tool.
LABEL HDDtools
Menu LABEL Hard Drive Testing Tools
kernel vesamenu.c32
append menu/hdd.cfg
TEXT HELP
Hard Drive Diagnostic Tools
ENDTEXT
Now we need to make a file called hdd.cfg in side the menu folder and make it boot our images. Place all these files inside the util folder for img and other image files and place iso in side of the iso folder. Link to them accordingly.
Contents of hdd.cfg
if we want to boot an iso we want to do a
LABEL AcronisDiskDirector
LINUX memdisk
APPEND iso
INITRD iso/Adds.iso
We can also boot basically anything we want just need to create a menu system. That will take us there. We can also add a password to the menu system if we don’t want someone to get access to certain things.
MENU PASSWD passwd
(Only valid after a LABEL statement, or a MENU BEGIN statement.)
Sets a password on this menu entry. "passwd" can be either a cleartext password, a SHA-1 encrypted password (starting with $4$), or and MD5 encrypted password (starting with $1$).
You can protect an entire submenu by using "MENU PASSWD" after the submenu's "MENU BEGIN."
Use the included Perl scripts "sha1pass" or "md5pass" to encrypt passwords. MD5 passwords are compatible with most Unix password file utilities; SHA-1 passwords are probably unique to SYSLINUX. Obviously, if you don't encrypt your passwords they will not be very secure at all.
If you are using passwords, you want to make sure you also use the settings "NOESCAPE 1", "PROMPT 0", and either set "ALLOWOPTIONS 0" or use a master password (see below.)
If passwd is an empty string, this menu entry can only be unlocked with the master password.
MENU MASTER PASSWD passwd
Sets a master password. This password can be used to boot any menu entry, and is required for the [Tab] and [Esc] keys to work.
To generate a password use openssl passwd -1 mypassword
Example:
In my case its test
Trouble shooting:
If you get an unmountable boot volume its cause there is no ramdisk options in your bcd config please reread the instructions on how to setup bcd.
Network card is not detected in pxe env. Go to manufactures website and download there network card driver, and run the add driver commands.
If you get a ip fragment please open up your registery and goto [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\Tcpip\Parameters\Interfaces\guid for my network card
and setting MTU to 1492 and rebooting the system once you do that error should resolve its self.
If you get a gray screen on the syslinux menu its problem because the name was spelled wrong. Check the tftp log and correct spelling if it is the case.
So my wife got me this awesome Star Trek Enterprise model with working lights and a play able recording of the intro to the original series for $10 at a rummage sale. Only issue was the batteries have been in there for ages and was all busted open, acid all over, and crossion everywhere inside. I did my best to clean it all but still it was a mess. Rather then wasting more batteries I decided to make a little modification and have it run off of USB power! The voltage is just about the same, the model runs off 4.5v and USB outputs around 5v “this will vary from machine to machine, even port to port in some cases”. For example when I hooked it up to my laptop the brightness and everything was perfect, but when I connected to a desktop machine at work the lights got very bright and hot fast, I solved this by attaching a non-powered USB hub and connecting the model to that. Below are a few pictures I took from the mod. Ok that is it, enjoy!
Here is a close up of my new toy:

Here is the USB cable I used:

Here is the cable attached to the base:

Here is the cable soldered to the main board in the base:

And here is the finished project:

Well Novembers meeting was one of our best for sure! Many thanks to James and Bucketworks for putting the safe opening event together and letting us play with your locks and junk, you are the best! It all started with everyone just fucking off enjoying some snacks, cold beers, and some tunes. Then Klaiviel and James got the party started.
Klaiviel gave us a little intro to the safe, its lock, and some of the history all the while James was playing the roll of Geraldo all too well and dropping the lulz like no one. Once the safe was open there was a mad dash to see what was inside!! Lots of brooms, paper and some beta tapes suspected to be vintage pron. Cmoney took lots of pictures and video “below” of the safe opening.
After the party died down a little bit we talked about a issue one of our members is having with china and how to resolve them. Then ngharo and I gave a small demo on physical security and some of the tools one might use. We focused on Switchblade and an Arduino USB keyboard emulator “this is a post for another day” to pwn the shit out of windows, man that was fun. Ok thats it, peace.
F4r4d4y jr won an IE6 admin pack

The following videos are just og the safe opening and viewing of the contents:
pt1
pt2
Full video of the party
http://www.ustream.tv/recorded/18313140